Generate Client Certificate With Ca Key
- Generate Client Certificate With Ca Keys
- Generate Ssl Client Certificate
- Generate Client Id And Secret
- Generate Client Certificate With Ca Key Vs
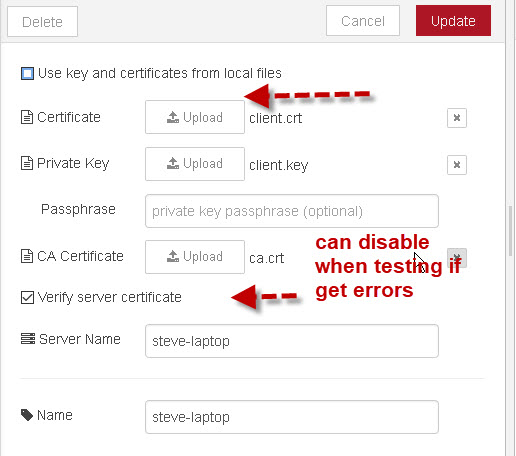
- Install Client Certificate For Authentication
Crt and key files represent both parts of a certificate, key being the private key to the certificate and crt being the signed certificate. It's only one of the ways to generate certs, another way would be having both inside a pem file or another in a p12 container. Create a certificate ¶ Use the private key to create a certificate signing request (CSR). The CSR details don’t need to match the intermediate CA. For server certificates, the Common Name must be a fully qualified domain name (eg, www.example.com), whereas for client certificates it can be any unique identifier (eg, an e-mail address). I am trying to create client certifications against a Microsoft CA using the built in website. (Microsoft Active Directory Certificate Services) From what I can tell, you have to login as the user to. Creating Client Certificate - Windows. Ask Question Asked 9 years, 10 months ago. Http client certificates vs ssh public keys. As a result, the certificate isn't an available option for specifying the server certificate or client certificate when you create the AWS Client VPN endpoint. Import the server and client certificates and keys into ACM. Note: The server and client certificates, and their respective keys, are available in C:Program FilesOpenVPNeasy-rsakeys.
At the prompt, change the Common Name to your client's domain name using the format client2.example.com. Leave all of the remaining fields as the default values.
Important: If you don't follow the format specified above for setting common names, the domain names aren't available when you import the certificate into ACM. As a result, the certificate isn't an available option for specifying the server certificate or client certificate when you create the AWS Client VPN endpoint.
Import the server and client certificates and keys into ACM
Note: The server and client certificates, and their respective keys, are available in C:Program FilesOpenVPNeasy-rsakeys. /windows-10-product-key-generator-32-bit.html.
1. Open the following files: server.crt, server.key, client1.crt, client1.key, and ca.crt. https://usacuba.weebly.com/home/download-windows-rdc-for-mac.
2. Open the ACM console, and then choose Import a certificate.
3. On the Import a certificate page, copy/paste the content:
From the server.crt file to Certificate body.
From the server.key file to Certificate private key.
From the ca.crt file to Certificate chain.
4. Choose Import to import the server certificate.
Generate Client Certificate With Ca Keys
5. Choose Import a certificate again and copy/paste the content:
From the client1.crt file to Certificate body.
From the client1.key file to Certificate private key.
From the ca.crt fileto Certificate chain.
6. Choose Import to import the client certificate.
Or, you can use the AWS Command Line Interface (AWS CLI) to import the server and client certificates and their keys into ACM:
SSL’s primary function on the Internet is to facilitate encryption and trust that allows a web browser to validate the authenticity of a web site. However, SSL works the other way around too – client SSL certificates can be used to authenticate a client to the web server. Think SSH public/private key pairs, if that is familiar to you. In this blog post I will outline the steps to create a certificate authority certificate, sign a server certificate and install it in Apache, and create a client cert in a format used by web browsers.
Installing an operating system and Apache is outside the scope of the blog post and I assume you have a functioning Apache install before we get started. I am using an Ubuntu 12.04.4 system in this blog post.
Generate Ssl Client Certificate
Generate a certificate authority (CA) cert
The first step is to generate a CA certificate. This CA certificate does not need to be generated on your web server – it can sit on whatever machine you will use to generate SSL certificates. Once created, the CA cert will act as the trusted authority for both your server and client certs. It is the equivalent of the Verisign or Comodos in the real world of SSL, however you wouldn’t want to use your CA cert for a major public website as its trust isn’t going to be built into browsers everywhere.
Generate your CA certificate using this command:
Then keep them secret – keep them safe. If someone were to get a hold of these files they would be able to generate server and client certs that would be trusted by our web server as it will be configured below.
Generate your Apache server SSL key and certificate
Now that we have our CA cert, we can generate the SSL certificate that will be used by Apache.
- Generate a server private key.
- Use the server private key to generate a certificate generation request.
- Use the certificate generation request and the CA cert to generate the server cert.
- Clean up – now that the cert has been created, we no longer need the request.
Install the server certificate in Apache
My server is running Ubuntu 12.04.4 so all paths and commands referenced here are for that operating system.
- Copy the CA cert to a permanent place. We’ll need to specify our CA cert in Apache since it is a self generated CA and not one that is included in operating systems everywhere.
- Copy the server cert and private key to permanent place.
- Activate the SSL module in Apache.
- Activate the SSL site in Apache and disable the HTTP site.
- Edit /etc/apache2/sites-enabled/000-default-ssl (the config file for the SSL enabled site) and add:
- Apply the config in Apache.
Right now if you visit your https site, you will get an SSL error similar to “SSL peer was unable to negotiate an acceptable set of security parameters.” That is good – it means your site won’t accept a connection unless your browser is using a trusted client cert. We’ll generate one now.
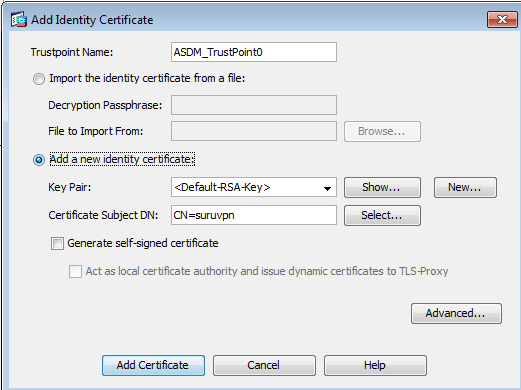
Generate a client SSL certificate
- Generate a private key for the SSL client.
- Use the client’s private key to generate a cert request.
- Issue the client certificate using the cert request and the CA cert/key.
- Convert the client certificate and private key to pkcs#12 format for use by browsers.
- Clean up – remove the client private key, client cert and client request files as the pkcs12 has everything needed.
Generate Client Id And Secret
Looks like a pretty similar process to generating a server certificate, huh?
Generate Client Certificate With Ca Key Vs
Lastly, import the .p12 file into your browser. On Windows you can double click the file to import into the operating system’s keystore that will be used by IE and Chrome. For Firefox, open the Options -> Advanced -> Certificates -> View Certificates -> Your Certificates and import the certificate.
Install Client Certificate For Authentication
Now, visit your website with the browser where you imported the client certificate. You’ll likely be prompted for which client certificate to use – select it. Then you’ll be authenticated and allowed in!