Generate S Mime Encryption Key
Oct 27, 2010 Simple Steps to Securing Email with S/MIME. The S/MIME standard is based on public-key cryptography. In this specification, an individual user owns a digital certificate which contains a. Outlook and Outlook Web App both support S/MIME. The S/MIME control is necessary to verify the signatures of digitally signed messages, but a certificate is not. If you receive a message that's been encrypted or digitally signed and you haven't installed the S/MIME control, you'll see a warning in the message header notifying you that the S.
| OSI model by layer |
|---|
|
|
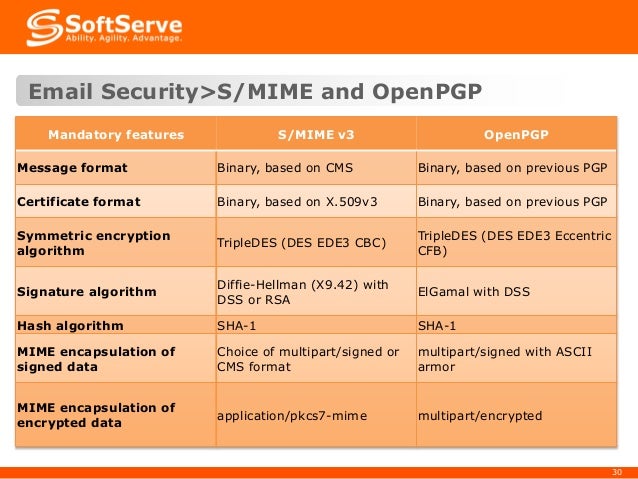
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a standard for public keyencryption and signing of MIME data. S/MIME is on an IETFstandards track and defined in a number of documents, most importantly RFC3369, 3370, 3850 and 3851. It was originally developed by RSA Data Security and the original specification used the IETF MIME specification[1] with the de facto industry standard PKCS#7 secure message format. Change control to S/MIME has since been vested in the IETF and the specification is now layered on Cryptographic Message Syntax (CMS), an IETF specification that is identical in most respects with PKCS #7. S/MIME functionality is built into the majority of modern email software and interoperates between them. Since it is built on CMS, MIME can also hold an advanced electronic signature.
Function[edit]
S/MIME provides the following cryptographic security services for electronic messaging applications:
- Message integrity
- Non-repudiation of origin (using digital signatures)
- Privacy
- Data security (using encryption)
S/MIME specifies the MIME type application/pkcs7-mime[2] (smime-type 'enveloped-data') for data enveloping (encrypting) where the whole (prepared) MIME entity to be enveloped is encrypted and packed into an object which subsequently is inserted into an application/pkcs7-mime MIME entity.
S/MIME certificates[edit]
Before S/MIME can be used in any of the above applications, one must obtain and install an individual key/certificate either from one's in-house certificate authority (CA) or from a public CA. The accepted best practice is to use separate private keys (and associated certificates) for signature and for encryption, as this permits escrow of the encryption key without compromise to the non-repudiation property of the signature key. Encryption requires having the destination party's certificate on store (which is typically automatic upon receiving a message from the party with a valid signing certificate). While it is technically possible to send a message encrypted (using the destination party certificate) without having one's own certificate to digitally sign, in practice, the S/MIME clients will require the user to install their own certificate before they allow encrypting to others. This is necessary so the message can be encrypted for both, recipient and sender, and a copy of the message can be kept (in the sent folder) and be readable for the sender.
A typical basic ('class 1') personal certificate verifies the owner's 'identity' only insofar as it declares that the sender is the owner of the 'From:' email address in the sense that the sender can receive email sent to that address, and so merely proves that an email received really did come from the 'From:' address given. It does not verify the person's name or business name. If a sender wishes to enable email recipients to verify the sender's identity in the sense that a received certificate name carries the sender's name or an organization's name, the sender needs to obtain a certificate ('class 2') from a CA who carries out a more in-depth identity verification process, and this involves making inquiries about the would-be certificate holder. For more detail on authentication, see digital signature.
Depending on the policy of the CA, the certificate and all its contents may be posted publicly for reference and verification. This makes the name and email address available for all to see and possibly search for. Other CAs only post serial numbers and revocation status, which does not include any of the personal information. The latter, at a minimum, is mandatory to uphold the integrity of the public key infrastructure.
Free S/MIME certificate issuers[edit]
Unrestricted use
- Actalis (1 year, no support for certificate signing requests)[3]
- WISeID (1 year, no support for certificate signing requests)[4]
- MeSince (renew certificates every 39 months)
Only for personal use (non-commercial)
- CAcert (6 months or 2 years; not widely trusted)
- Fossa.Me (3 months, not widely trusted)
Obstacles to deploying S/MIME in practice[edit]
- S/MIME is sometimes considered not properly suited for use via webmail clients. Though support can be hacked into a browser, some security practices require the private key to be kept accessible to the user but inaccessible from the webmail server, complicating the key advantage of webmail: providing ubiquitous accessibility. This issue is not fully specific to S/MIME: other secure methods of signing webmail may also require a browser to execute code to produce the signature; exceptions are PGP Desktop and versions of GnuPG, which will grab the data out of the webmail, sign it by means of a clipboard, and put the signed data back into the webmail page. Seen from the view of security this is a more secure solution.
- S/MIME is tailored for end-to-end security. Logically it is not possible to have a third party inspecting email for malware and also have secure end-to-end communications. Encryption will not only encrypt the messages, but also the malware. Thus if mail is not scanned for malware anywhere but at the end points, such as a company's gateway, encryption will defeat the detector and successfully deliver the malware. The only solution to this is to perform malware scanning on end user stations after decryption. Other solutions do not provide end-to-end trust as they require keys to be shared by a third party for the purpose of detecting malware. Examples of this type of compromise are:
- Solutions which store private keys on the gateway server so decryption can occur prior to the gateway malware scan. These unencrypted messages are then delivered to end users.
- Solutions which store private keys on malware scanners so that it can inspect messages content, the encrypted message is then relayed to its destination.
- Due to the requirement of a certificate for implementation, not all users can take advantage of S/MIME, as some may wish to encrypt a message, with a public/private key pair for example, without the involvement or administrative overhead of certificates.
Any message that an S/MIME email client stores encrypted cannot be decrypted if the applicable key pair's private key is unavailable or otherwise unusable (e.g., the certificate has been deleted or lost or the private key's password has been forgotten). However, an expired, revoked, or untrusted certificate will remain usable for cryptographic purposes. Indexing of encrypted messages' clear text may not be possible with all email clients. Neither of these potential dilemmas is specific to S/MIME but rather cipher text in general and do not apply to S/MIME messages that are only signed and not encrypted.
S/MIME signatures are usually 'detached signatures': the signature information is separate from the text being signed. The MIME type for this is multipart/signed with the second part having a MIME subtype of application/(x-)pkcs7-signature. Mailing list software is notorious for changing the textual part of a message and thereby invalidating the signature; however, this problem is not specific to S/MIME, and a digital signature only reveals that the signed content has been changed.
Security issues[edit]
On May 13, 2018, the Electronic Frontier Foundation (EFF) announced critical vulnerabilities in S/MIME, together with an obsolete form of PGP that is still used, in many email clients.[5] Dubbed EFAIL, this is a particularly critical hit to S/MIME that will require significant coordinated effort by many email client vendors to fix.[6]
See also[edit]
- DomainKeys Identified Mail for server-handled email message signing.
- EFAIL, a security issue in S/MIME
- GNU Privacy Guard (GPG)
- Pretty Good Privacy (PGP), especially 'MIME Security with OpenPGP' (RFC 3156).
References[edit]
- ^RFC 2045: Multipurpose Internet Mail Extensions (MIME). Part One was published in November 1996.
- ^Mission-critical Active Directory: Architecting a Secure and Scalable Infrastructure for Windows 2000. 2001. p. 550.
S/MIME adds new MIME content types that provide data confidentiality, integrity protection, nonrepudiation, and authentication services: application/pkcs7-mime, multipart/signed, and application/pkcs7-signature
- ^Roessli, David. 'Free S/MIME certificates in 2019', 19 December 2019. Retrieved on 17 February 2020.
- ^Zöchling, Frank. 'Tipp: Kostenloses S/MIME Zertifikat von WISeID' (German language), 30 January 2020. Retrieved on 17 February 2020.
- ^Gebhart, Danny O'Brien and Gennie (2018-05-13). 'Attention PGP Users: New Vulnerabilities Require You To Take Action Now'. Electronic Frontier Foundation. Retrieved 2018-05-29.
- ^Hansen, Robert (2018-05-20). 'Efail: A Postmortem'. Robert Hansen. Retrieved 2018-05-30.
External links[edit]
- RFC 5652: Cryptographic Message Syntax (CMS)
- RFC 3370: Cryptographic Message Syntax (CMS) Algorithms
- RFC 5751: Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 3.2 Message Specification
- RFC 8551: Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 4.0 Message Specification
- Microsoft Exchange Server: Understanding S/MIME (high-level overview).
As an administrator in Exchange Server, you can enable Secure/Multipurpose Internet Mail Extensions (S/MIME) for your organization. S/MIME is a widely accepted method (more precisely, a protocol) for sending digitally signed and encrypted messages. S/MIME allows you to encrypt emails and digitally sign them. When you use S/MIME, it helps the people who receive the message by:
Ensuring that the message in their inbox is the exact message that started with the sender.
Ensuring that the message came from the specific sender and not from someone pretending to be the sender.
To do this, S/MIME provides for cryptographic security services such as authentication, message integrity, and non-repudiation of origin (using digital signatures). S/MIME also helps enhance privacy and data security (using encryption) for electronic messaging.
S/MIME requires a certificate and publishing infrastructure that is often used in business-to-business and business-to-consumer situations. The user controls the cryptographic keys in S/MIME and can choose whether to use them for each message they send. Email programs such as Outlook search a trusted root certificate authority location to perform digital signing and verification of the signature.
For a more complete background about the history and architecture of S/MIME in the context of email, see Understanding S/MIME.
Generate S Mime Encryption Keys
Supported scenarios and technical considerations for S/MIME
You can set up S/MIME to work with any of the following end points:
Outlook 2010 or later
Outlook on the web (formerly known as Outlook Web App)
Exchange ActiveSync (EAS)
The steps that you follow to set up S/MIME with each of these endpoints are slightly different. Generally, you need to complete these steps:
Install a Windows-based Certification Authority and set up a public key infrastructure to issue S/MIME certificates. Certificates issued by third-party certificate providers are supported. For details, see Server Certificate Deployment Overview.
Publish the user certificate in an on-premises Active Directory Domain Services (AD DS) account in the UserSMIMECertificate and/or UserCertificate attributes. Your AD DS needs to be located on computers at a physical location that you control and not at a remote facility or cloud-based service somewhere on the Internet. For more information about AD DS, see Active Directory Domain Services Overview.
Set up a virtual certificate collection in order to validate S/MIME. This information is used by Outlook on the web when validating the signature of an email and ensuring that it was signed by a trusted certificate.
Set up the Outlook or EAS end point to use S/MIME.
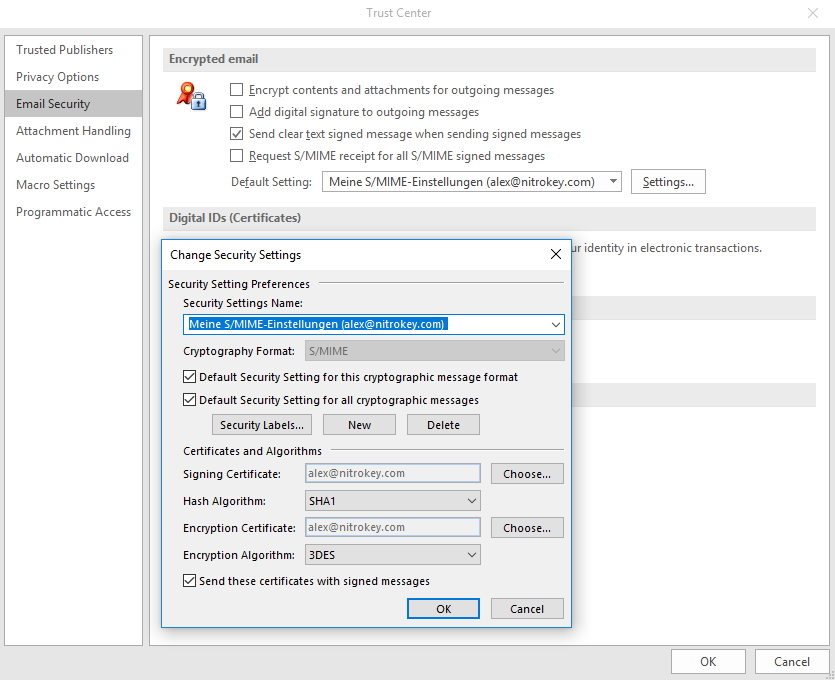
Set up S/MIME with Outlook on the web
Smash bros crusade download mac. Setting up S/MIME with Outlook on the web involves these key steps:
S/MIME settings for Outlook on the web in Exchange Server.
For information about how to send an S/MIME encrypted message in Outlook on the web, see Encrypt messages by using S/MIME in Outlook on the web.
Related message encryption technologies
Generate S Mime Encryption Key Software
/fifa-18-keygen-cd-key-generator.html. A variety of encryption technologies work together to provide protection for messages at rest and in transit. S/MIME can work simultaneously with the following technologies but isn't dependent on them:
S Mime Encryption
Transport Layer Security (TLS): Encrypts the tunnel or the route between email servers in order to help prevent snooping and eavesdropping, and encrypts the connection between email clients and servers.
Note
Secure Sockets Layer (SSL) is being replaced by Transport Layer Security (TLS) as the protocol that's used to encrypt data sent between computer systems. They're so closely related that the terms 'SSL' and 'TLS' (without versions) are often used interchangeably. Because of this similarity, references to 'SSL' in Exchange topics, the Exchange admin center, and the Exchange Management Shell have often been used to encompass both the SSL and TLS protocols. Typically, 'SSL' refers to the actual SSL protocol only when a version is also provided (for example, SSL 3.0). To find out why you should disable the SSL protocol and switch to TLS, check out Protecting you against the SSL 3.0 vulnerability.
BitLocker: Encrypts the data on a hard drive in a datacenter so that if someone gets unauthorized access, they can't read it. For more information, see BitLocker: How to deploy on Windows Server 2012 and later