Minisign Generate A New Key Pair Dnscrypt
With a secure shell (SSH) key pair, you can create virtual machines (VMs) in Azure that use SSH keys for authentication, eliminating the need for passwords to sign in. This article shows you how to quickly generate and use an SSH public-private key file pair for Linux VMs. You can complete these steps with the Azure Cloud Shell, a macOS or Linux host, the Windows Subsystem for Linux, and other tools that support OpenSSH.
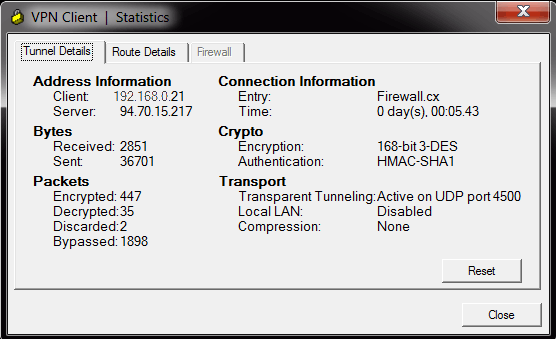
Simple DNSCrypt A simple management tool for dnscrypt-proxy Download.msi (x64 Installer) Download.msi (x86 Installer) View on GitHub Download.zip Download.tar.gz Simple DNSCrypt. Simple DNSCrypt is a simple management tool to configure dnscrypt-proxy on windows based systems. Generating Keys for Encryption and Decryption.; 3 minutes to read +7; In this article. Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data.
Note
https://bbentrancement.weebly.com/blog/download-fate-hollow-ataraxia. VMs created using SSH keys are by default configured with passwords disabled, which greatly increases the difficulty of brute-force guessing attacks.
For more background and examples, see Detailed steps to create SSH key pairs.
For additional ways to generate and use SSH keys on a Windows computer, see How to use SSH keys with Windows on Azure.
Supported SSH key formats
Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported.
Create an SSH key pair
Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the ~/.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten.
The following command creates an SSH key pair using RSA encryption and a bit length of 4096:
If you use the Azure CLI to create your VM with the az vm create command, you can optionally generate SSH public and private key files using the --generate-ssh-keys option. The key files are stored in the ~/.ssh directory unless specified otherwise with the --ssh-dest-key-path option. The --generate-ssh-keys option will not overwrite existing key files, instead returning an error. In the following command, replace VMname and RGname with your own values:
Provide an SSH public key when deploying a VM
To create a Linux VM that uses SSH keys for authentication, specify your SSH public key when creating the VM using the Azure portal, Azure CLI, Azure Resource Manager templates, or other methods:
If you're not familiar with the format of an SSH public key, you can display your public key with the following cat command, replacing ~/.ssh/id_rsa.pub with the path and filename of your own public key file if needed:
A typical public key value looks like this example:
If you copy and paste the contents of the public key file to use in the Azure portal or a Resource Manager template, make sure you don't copy any trailing whitespace. To copy a public key in macOS, you can pipe the public key file to pbcopy. Similarly in Linux, you can pipe the public key file to programs such as xclip.
The public key that you place on your Linux VM in Azure is by default stored in ~/.ssh/id_rsa.pub, unless you specified a different location when you created the key pair. To use the Azure CLI 2.0 to create your VM with an existing public key, specify the value and optionally the location of this public key using the az vm create command with the --ssh-key-values option. In the following command, replace VMname, RGname, and keyFile with your own values:
If you want to use multiple SSH keys with your VM, you can enter them in a space-separated list, like this --ssh-key-values sshkey-desktop.pub sshkey-laptop.pub.
SSH into your VM
With the public key deployed on your Azure VM, and the private key on your local system, SSH into your VM using the IP address or DNS name of your VM. In the following command, replace azureuser and myvm.westus.cloudapp.azure.com with the administrator user name and the fully qualified domain name (or IP address):
If you specified a passphrase when you created your key pair, enter that passphrase when prompted during the login process. The VM is added to your ~/.ssh/known_hosts file, and you won't be asked to connect again until either the public key on your Azure VM changes or the server name is removed from ~/.ssh/known_hosts.
If the VM is using the just-in-time access policy, you need to request access before you can connect to the VM. For more information about the just-in-time policy, see Manage virtual machine access using the just in time policy.
Next steps
Mini Sign Generate A New Key Pair Dnscrypt
For more information on working with SSH key pairs, see Detailed steps to create and manage SSH key pairs.
If you have difficulties with SSH connections to Azure VMs, see Troubleshoot SSH connections to an Azure Linux VM.
Minisign Generate A New Key Pair Dnscrypt Key
- ##############################################
- # dnscrypt-proxy configuration #
- ##############################################
- ## This is an example configuration file.
- ## You should adjust it to your needs, and save it as 'dnscrypt-proxy.toml'
- ## Online documentation is available here: https://dnscrypt.info/doc
- ##################################
- ##################################
- cert_ignore_timestamp = true
- ## List of servers to use
- ## Servers from the 'public-resolvers' source (see down below) can
- ## be viewed here: https://dnscrypt.info/public-servers
- ## If this line is commented, all registered servers matching the require_* filters
- ##
- ## The proxy will automatically pick the fastest, working servers from the list.
- ## Remove the leading # first to enable this; lines starting with # are ignored.
- server_names = ['quad9-dnscrypt-ip4-nofilter-pri', 'quad9-dnscrypt-ip4-nofilter-alt']
- ## List of local addresses and ports to listen to. Can be IPv4 and/or IPv6.
- listen_addresses = ['127.0.0.1:65053']
- ## Maximum number of simultaneous client connections to accept
- max_clients = 1024
- ## Switch to a different system user after listening sockets have been created.
- ## Note (1): this feature is currently unsupported on Windows.
- ## Note (2): this feature is not compatible with systemd socket activation.
- ## Note (3): when using -pidfile, the PID file directory must be writable by the new user
- user_name = 'nobody'
- ## Require servers (from static + remote sources) to satisfy specific properties
- # Use servers reachable over IPv4
- # Use servers reachable over IPv6 -- Do not enable if you don't have IPv6 connectivity
- dnscrypt_servers = true
- # Use servers implementing the DNS-over-HTTPS protocol
- ## Require servers defined by remote sources to satisfy specific properties
- # Server must support DNS security extensions (DNSSEC)
- require_nolog = true
- # Server must not enforce its own blacklist (for parental control, ads blocking..)
- # Server names to avoid even if they match all criteria
- ## Always use TCP to connect to upstream servers.
- ## This can be useful if you need to route everything through Tor.
- ## Otherwise, leave this to `false`, as it doesn't improve security
- ## (dnscrypt-proxy will always encrypt everything even using UDP), and can
- ## SOCKS proxy
- ## Uncomment the following line to route all TCP connections to a local Tor node
- ## Tor doesn't support UDP, so set `force_tcp` to `true` as well.
- # proxy = 'socks5://127.0.0.1:9050'
- ## Only for DoH servers
- # http_proxy = 'http://127.0.0.1:8888'
- ## How long a DNS query will wait for a response, in milliseconds.
- ## If you have a network with *a lot* of latency, you may need to
- ## increase this. Startup may be slower if you do so.
- ## Don't increase it too much. 10000 is the highest reasonable value.
- timeout = 5000
- ## Keepalive for HTTP (HTTPS, HTTP/2) queries, in seconds
- keepalive = 120
- ## Response for blocked queries. Options are `refused`, `hinfo` (default) or
- ## an IP response. To give an IP response, use the format `a:<IPv4>,aaaa:<IPv6>`.
- ## Using the `hinfo` option means that some responses will be lies.
- ## Unfortunately, the `hinfo` option appears to be required for Android 8+
- # blocked_query_response = 'refused'
- ## Load-balancing strategy: 'p2' (default), 'ph', 'first' or 'random'
- lb_strategy = 'p2'
- ## Set to `true` to constantly try to estimate the latency of all the resolvers
- ## and adjust the load-balancing parameters accordingly, or to `false` to disable.
- # lb_estimator = true
- ## Log level (0-6, default: 2 - 0 is very verbose, 6 only contains fatal errors)
- log_level = 1
- ## Use the system logger (syslog on Unix, Event Log on Windows)
- # use_syslog = true
- ## Delay, in minutes, after which certificates are reloaded
- cert_refresh_delay = 240
- ## DNSCrypt: Create a new, unique key for every single DNS query
- ## This may improve privacy but can also have a significant impact on CPU usage
- ## Only enable if you don't have a lot of network load
- # dnscrypt_ephemeral_keys = false
- ## DoH: Disable TLS session tickets - increases privacy but also latency
- # tls_disable_session_tickets = false
- ## DoH: Use a specific cipher suite instead of the server preference
- ## 49195 = TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- ## 52393 = TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305
- ## 4867 = TLS_CHACHA20_POLY1305_SHA256
- ## On non-Intel CPUs such as MIPS routers and ARM systems (Android, Raspberry Pi..),
- ## This may also help on Intel CPUs running 32-bit operating systems.
- ## Keep tls_cipher_suite empty if you have issues fetching sources or
- ## connecting to some DoH servers. Google and Cloudflare are fine with it.
- # tls_cipher_suite = [52392, 49199]
- ## This is a normal, non-encrypted DNS resolver, that will be only used
- ## for one-shot queries when retrieving the initial resolvers list, and
- ## only if the system DNS configuration doesn't work.
- ## No user application queries will ever be leaked through this resolver,
- ## and it will not be used after IP addresses of resolvers URLs have been found.
- ## It will never be used if lists have already been cached, and if stamps
- ## It will not be used if the configured system DNS works.
- ##
- ## People in China may need to use 114.114.114.114:53 here.
- ## Other popular options include 8.8.8.8 and 1.1.1.1.
- fallback_resolver = '8.8.8.8:53'
- ## Always use the fallback resolver before the system DNS settings
- ignore_system_dns = true
- ## Maximum time (in seconds) to wait for network connectivity before
- ## Useful if the proxy is automatically started at boot, and network
- ## connectivity is not guaranteed to be immediately available.
- ## Use 0 to not test for connectivity at all (not recommended),
- ## Address and port to try initializing a connection to, just to check
- ## if the network is up. It can be any address and any port, even if
- ## there is nothing answering these on the other side. Just don't use
- ## a local address, as the goal is to check for Internet connectivity.
- ## On Windows, a datagram with a single, nul byte will be sent, only
- ## On other operating systems, the connection will be initialized
- ## Offline mode - Do not use any remote encrypted servers.
- ## The proxy will remain fully functional to respond to queries that
- ## plugins can handle directly (forwarding, cloaking, ..)
- # offline_mode = false
- ## These strings will be added as TXT records to queries.
- ## Do not use, except on servers explicitly asking for extra data
- # query_meta = ['key1:value1', 'key2:value2', 'key3:value3']
- # Maximum log files size in MB - Set to 0 for unlimited.
- log_files_max_age = 7
- # Maximum log files backups to keep (or 0 to keep all backups)
- # Filters #
- ## Immediately respond to IPv6-related queries with an empty response
- ## This makes things faster when there is no IPv6 connectivity, but can
- ## also cause reliability issues with some stub resolvers.
- ## Do not enable if you added a validating resolver such as dnsmasq in front
- ## TTL for synthetic responses sent when a request has been blocked (due to
- ##################################################################################
- # Route queries for specific domains to a dedicated set of servers #
- ##################################################################################
- ## Example map entries (one entry per line):
- ## example.net 9.9.9.9,8.8.8.8,1.1.1.1
- # forwarding_rules = 'forwarding-rules.txt'
- ###############################
- ###############################
- ## Cloaking returns a predefined address for a specific name.
- ## In addition to acting as a HOSTS file, it can also return the IP address
- ## of a different name. It will also do CNAME flattening.
- ## Example map entries (one entry per line)
- ## www.google.com forcesafesearch.google.com
- # cloaking_rules = 'cloaking-rules.txt'
- ## TTL used when serving entries in cloaking-rules.txt
- # cloak_ttl = 600
- # DNS cache #
- ## Enable a DNS cache to reduce latency and outgoing traffic
- cache = true
- ## Minimum TTL for cached entries
- cache_min_ttl = 600
- ## Minimum TTL for negatively cached entries
- cache_neg_min_ttl = 60
- # Query logging #
- ## Path to the query log file (absolute, or relative to the same directory as the executable file)
- ## Can be /dev/stdout to log to the standard output (and set log_files_max_size to 0)
- # file = 'query.log'
- ## Query log format (currently supported: tsv and ltsv)
- format = 'tsv'
- ## Do not log these query types, to reduce verbosity. Keep empty to log everything.
- # ignored_qtypes = ['DNSKEY', 'NS']
- ############################################
- ############################################
- ## Log queries for nonexistent zones
- ## These queries can reveal the presence of malware, broken/obsolete applications,
- ## and devices signaling their presence to 3rd parties.
- [nx_log]
- ## Path to the query log file (absolute, or relative to the same directory as the executable file)
- # file = 'nx.log'
- ## Query log format (currently supported: tsv and ltsv)
- format = 'tsv'
- ######################################################
- ######################################################
- ## Blacklists are made of one pattern per line. Example of valid patterns:
- ## example.com
- ## *sex*
- ## ads*.example.*
- ##
- ## Example blacklist files can be found at https://download.dnscrypt.info/blacklists/
- ## A script to build blacklists from public feeds can be found in the
- ## `utils/generate-domains-blacklists` directory of the dnscrypt-proxy source code.
- [blacklist]
- ## Path to the file of blocking rules (absolute, or relative to the same directory as the executable file)
- # blacklist_file = 'blacklist.txt'
- ## Optional path to a file logging blocked queries
- # log_file = 'blocked.log'
- ## Optional log format: tsv or ltsv (default: tsv)
- # log_format = 'tsv'
- ###########################################################
- ###########################################################
- ## IP blacklists are made of one pattern per line. Example of valid patterns:
- ## 127.*
- ## 192.168.1.4
- [ip_blacklist]
- ## Path to the file of blocking rules (absolute, or relative to the same directory as the executable file)
- # blacklist_file = 'ip-blacklist.txt'
- ## Optional path to a file logging blocked queries
- # log_file = 'ip-blocked.log'
- ## Optional log format: tsv or ltsv (default: tsv)
- # log_format = 'tsv'
- ######################################################
- # Pattern-based whitelisting (blacklists bypass) #
- ######################################################
- ## Whitelists support the same patterns as blacklists
- ## If a name matches a whitelist entry, the corresponding session
- ##
- ## Time-based rules are also supported to make some websites only accessible at specific times of the day.
- [whitelist]
- ## Path to the file of whitelisting rules (absolute, or relative to the same directory as the executable file)
- # whitelist_file = 'whitelist.txt'
- ## Optional path to a file logging whitelisted queries
- # log_file = 'whitelisted.log'
- ## Optional log format: tsv or ltsv (default: tsv)
- # log_format = 'tsv'
- ##########################################
- ##########################################
- ## One or more weekly schedules can be defined here.
- ## Patterns in the name-based blocklist can optionally be followed with @schedule_name
- ## to apply the pattern 'schedule_name' only when it matches a time range of that schedule.
- ## For example, the following rule in a blacklist file:
- ## would block access to YouTube only during the days, and period of the days
- ##
- ## {after='21:00', before= '7:00'} matches 0:00-7:00 and 21:00-0:00
- ## {after= '9:00', before='18:00'} matches 9:00-18:00
- [schedules]
- # [schedules.'time-to-sleep']
- # tue = [{after='21:00', before='7:00'}]
- # thu = [{after='21:00', before='7:00'}]
- # sat = [{after='23:00', before='7:00'}]
- # mon = [{after='9:00', before='18:00'}]
- # wed = [{after='9:00', before='18:00'}]
- # fri = [{after='9:00', before='17:00'}]
- #########################
- #########################
- ## Remote lists of available servers
- ## Multiple sources can be used simultaneously, but every source
- ##
- ## Refer to the documentation for URLs of public sources.
- ## A prefix can be prepended to server names in order to
- ## avoid collisions if different sources share the same for
- ## different servers. In that case, names listed in `server_names`
- ##
- ## If the `urls` property is missing, cache files and valid signatures
- ## must be already present; This doesn't prevent these cache files from
- ## An example of a remote source from https://github.com/DNSCrypt/dnscrypt-resolvers
- [sources.'public-resolvers']
- urls = ['https://raw.githubusercontent.com/DNSCrypt/dnscrypt-resolvers/master/v2/public-resolvers.md', 'https://download.dnscrypt.info/resolvers-list/v2/public-resolvers.md']
- minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3'
- urls = ['https://raw.githubusercontent.com/DNSCrypt/dnscrypt-resolvers/master/v2/relays.md', 'https://download.dnscrypt.info/resolvers-list/v2/relays.md']
- minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3'
- prefix = '
- ## Quad9 over DNSCrypt - https://quad9.net/
- # [sources.quad9-resolvers]
- # urls = ['https://www.quad9.net/quad9-resolvers.md']
- # minisign_key = 'RWQBphd2+f6eiAqBsvDZEBXBGHQBJfeG6G+wJPPKxCZMoEQYpmoysKUN'
- # prefix = 'quad9-'
- ## Another example source, with resolvers censoring some websites not appropriate for children
- ## This is a subset of the `public-resolvers` list, so enabling both is useless
- # [sources.'parental-control']
- # urls = ['https://raw.githubusercontent.com/DNSCrypt/dnscrypt-resolvers/master/v2/parental-control.md', 'https://download.dnscrypt.info/resolvers-list/v2/parental-control.md']
- # minisign_key = 'RWQf6LRCGA9i53mlYecO4IzT51TGPpvWucNSCh1CBM0QTaLn73Y7GFO3'
- # Servers with known bugs #
- # Cisco servers currently cannot handle queries larger than 1472 bytes, and don't
- # truncate reponses larger than questions as expected by the DNSCrypt protocol.
- # This prevents large responses from being received, and breaks relaying.
- # A workaround for the first issue will be applied to servers in list below.
- # Do not change that list until the bugs are fixed server-side.
- broken_query_padding = ['cisco', 'cisco-ipv6', 'cisco-familyshield']
- # Anonymized DNS #
- ## Routes are indirect ways to reach DNSCrypt servers.
- ## A route maps a server name ('server_name') to one or more relays that will be
- ##
- ## A relay can be specified as a DNS Stamp (either a relay stamp, or a
- ## DNSCrypt stamp), an IP:port, a hostname:port, or a server name.
- ## The following example routes 'example-server-1' via `anon-example-1` or `anon-example-2``,
- ## and 'example-server-2' via the relay whose relay DNS stamp
- ##
- ##
- ## Review the list of available relays from the 'relays.md` file, and, for each
- ## server you want to use, define the relays you want connections to go through.
- ## Carefully choose relays and servers so that the are run by different entities.
- ## 'server_name' can also be set to '*' to define a default route, but this is not
- ## recommended. if you do so, keep 'server_names' short and distinct from relays.
- routes = [
- { server_name='quad9-dnscrypt-ip4-nofilter-pri', via=['anon-cs-usca'] },
- { server_name='quad9-dnscrypt-ip4-nofilter-alt', via=['anon-cs-usca'] }
- # { server_name='example-server-1', via=['anon-example-1', 'anon-example-2'] },
- # { server_name='example-server-2', via=['sdns://gRIxMzcuNzQuMjIzLjIzNDo0NDM'] }
- ## Optional, local, static list of additional servers
- # stamp = 'sdns:AQcAAAAAAAAAAAAQMi5kbnNjcnlwdC1jZXJ0Lg'