Service Primary Key Avoid Auto Generate
- Service Primary Key Avoid Auto Generate Data
- Service Primary Key Avoid Auto Generate In Excel
- Service Primary Key Avoid Auto Generate Money
- Service Primary Key Avoid Auto Generate Number
Similar to MySQL, PostgreSQL, Oracle, and many other relational databases, SQL Server is best utilized when assigning unique primary keys to most database tables.
The advantages to using numeric, auto incremented primary keys are numerous, but the most impactful benefits are faster speed when performing queries and data-independence when searching through thousands of records which might contain frequently altered data elsewhere in the table. With a consistent and unique numeric identifier, applications can take advantage of these faster and more reliable queries.
Basic Table Creation
Once connected to your SQL Server, you’d normally start by CREATING a new table that contains the the field you wish to use as your incremented primary key. For our example, we’ll stick with the tried and true id field:
Aug 08, 2017 Supported types for a primary key. A simple primary key field or one of the composite primary key field should be one of the following types: Any Java primitive type; any Any primitive wrapper type; java.lang.String; java.util.Date; java.sql.Date; java.math.BigDecimal; java.math.BigInteger; In this tutorial we are going to focus on generation strategies of simple primary key. Are they also stored as the primary key at the database level. That's where you should stop, right there, and rethink. Your database primary key should NEVER have business meaning. It should be meaningless by definition. So add the GUID as your business key, and a normal primary key (usually a long int) as the database primary key. Jan 24, 2017 Introduction. As I already mentioned, you should never use the TABLE identifier generator since it does not scale properly.In this post, I’ll show you why you should not rely on the AUTO GenerationType strategy if you’re Hibernate application uses MySQL. Prior to Hibernate 5. On Hibernate 4, if you had the following entity mapping.
The problem here is, we have no way of controlling our id field. When a new record is inserted, we not only must manually enter a value for id, but we have to perform a query ahead of time to attempt to verify that id value doesn’t already exist (a near-impossibility when dealing with many simultaneous connections).
Using Identity and Primary Key Constraints
The solution turns out to be using two constraint options provided by SQL Server.
The first is PRIMARY KEY, which as the name suggests, forces the specified column to behave as a completely unique index for the table, allowing for rapid searching and queries.
While SQL Server only allows one PRIMARY KEY constraint assigned to a single table, that PRIMARY KEY can be defined for more than one column. In a multi-column scenario, individual columns can contain duplicate, non-unique values, but the PRIMARY KEY constraint ensures that every combination of constrained values will in fact be unique relative to every other combination.
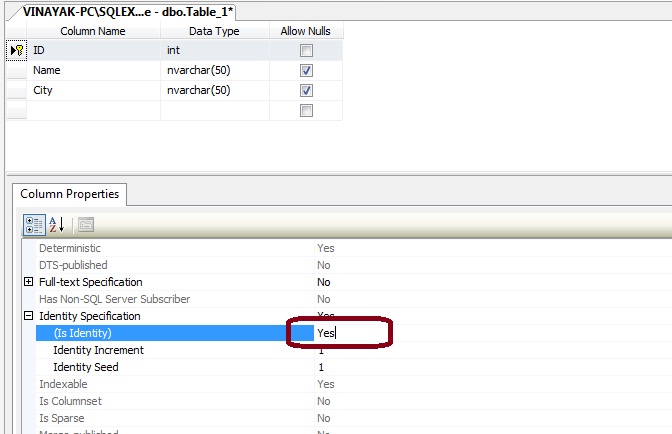
The second piece of the puzzle is the IDENTITY constraint, which informs SQL Server to auto increment the numeric value within the specified column anytime a new record is INSERTED. While IDENTITYcan accept two arguments of the numeric seed where the values will begin from as well as the increment, these values are typically not specified with the IDENTITY constraint and instead are left as defaults (both default to 1).
With this new knowledge at our fingertips, we can rewrite our previous CREATE TABLE statement by adding our two new constraints.
That’s all there is to it. Now the id column of our books table will be automatically incremented upon every INSERT and the id field is guaranteed to be a unique value as well.
All requests to a search service need a read-only api-key that was generated specifically for your service. The api-key is the sole mechanism for authenticating access to your search service endpoint and must be included on every request. In REST solutions, the api-key is typically specified in a request header. In .NET solutions, a key is often specified as a configuration setting and then passed as Credentials (admin key) or SearchCredentials (query key) on SearchServiceClient.
Keys are created with your search service during service provisioning. You can view and obtain key values in the Azure portal.
What is an api-key
An api-key is a string composed of randomly generated numbers and letters. Through role-based permissions, you can delete or read the keys, but you can't replace a key with a user-defined password or use Active Directory as the primary authentication methodology for accessing search operations.
Two types of keys are used to access your search service: admin (read-write) and query (read-only).
| Key | Description | Limits |
|---|---|---|
| Admin | Grants full rights to all operations, including the ability to manage the service, create and delete indexes, indexers, and data sources. Two admin keys, referred to as primary and secondary keys in the portal, are generated when the service is created and can be individually regenerated on demand. Having two keys allows you to roll over one key while using the second key for continued access to the service. Admin keys are only specified in HTTP request headers. You cannot place an admin api-key in a URL. | Maximum of 2 per service |
| Query | Grants read-only access to indexes and documents, and are typically distributed to client applications that issue search requests. Query keys are created on demand. You can create them manually in the portal or programmatically via the Management REST API. Query keys can be specified in an HTTP request header for search, suggestion, or lookup operation. Alternatively, you can pass a query key as a parameter on a URL. Depending on how your client application formulates the request, it might be easier to pass the key as a query parameter: GET /indexes/hotels/docs?search=*&$orderby=lastRenovationDate desc&api-version=2019-05-06&api-key=[query key] | 50 per service |
Visually, there is no distinction between an admin key or query key. Both keys are strings composed of 32 randomly generated alpha-numeric characters. If you lose track of what type of key is specified in your application, you can check the key values in the portal or use the REST API to return the value and key type.
Note
It is considered a poor security practice to pass sensitive data such as an api-key in the request URI. For this reason, Azure Cognitive Search only accepts a query key as an api-key in the query string, and you should avoid doing so unless the contents of your index should be publicly available. As a general rule, we recommend passing your api-key as a request header.
Find existing keys
Service Primary Key Avoid Auto Generate Data
You can obtain access keys in the portal or through the Management REST API. For more information, see Manage admin and query api-keys.
Sign in to the Azure portal.
List the search services for your subscription.
Select the service and on the Overview page, click Settings >Keys to view admin and query keys.
Create query keys
Service Primary Key Avoid Auto Generate In Excel
Query keys are used for read-only access to documents within an index for operations targeting a documents collection. Ghost recon advanced warfighter 2 serial key generator. Search, filter, and suggestion queries are all operations that take a query key. Any read-only operation that returns system data or object definitions, such as an index definition or indexer status, requires an admin key.
Restricting access and operations in client apps is essential to safeguarding the search assets on your service. Always use a query key rather than an admin key for any query originating from a client app.
Sign in to the Azure portal.
List the search services for your subscription.
Select the service and on the Overview page, click Settings >Keys.
Click Manage query keys.
Use the query key already generated for your service, or create up to 50 new query keys. The default query key is not named, but additional query keys can be named for manageability.
Note
A code example showing query key usage can be found in Query an Azure Cognitive Search index in C#.
Regenerate admin keys
Two admin keys are created for each service so that you can rotate a primary key, using the secondary key for business continuity.
- In the Settings >Keys page, copy the secondary key.
- For all applications, update the api-key settings to use the secondary key.
- Regenerate the primary key.
- Update all applications to use the new primary key.
If you inadvertently regenerate both keys at the same time, all client requests using those keys will fail with HTTP 403 Forbidden. However, content is not deleted and you are not locked out permanently.
You can still access the service through the portal or the management layer (REST API, PowerShell, or Azure Resource Manager). Management functions are operative through a subscription ID not a service api-key, and thus still available even if your api-keys are not.
After you create new keys via portal or management layer, access is restored to your content (indexes, indexers, data sources, synonym maps) once you have the new keys and provide those keys on requests.
Secure api-keys
Key security is ensured by restricting access via the portal or Resource Manager interfaces (PowerShell or command-line interface). As noted, subscription administrators can view and regenerate all api-keys. As a precaution, review role assignments to understand who has access to the admin keys.
- In the service dashboard, click Access control (IAM) and then the Role assignments tab to view role assignments for your service.
Members of the following roles can view and regenerate keys: Owner, Contributor, Search Service Contributors
Service Primary Key Avoid Auto Generate Money
Note
Service Primary Key Avoid Auto Generate Number
For identity-based access over search results, you can create security filters to trim results by identity, removing documents for which the requestor should not have access. For more information, see Security filters and Secure with Active Directory.